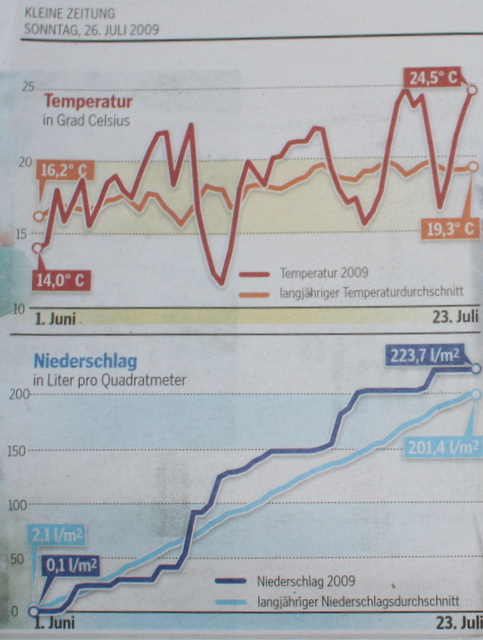
While messing around with X.509 certificates I not only encountered Umlauts, but Extended Validation Certificates as well. All nice and dandy, but these contain special OIDs in the subject field which openssl does not know the name.
Googling around I found a few references to their names, but no definitive source (especially for a short-name).
Anyway, the OIDs in question are under 1.3.6.1.4.1.311.60.2.1. So who is responsible for that OID tree? First step IANA, where we find the OID registry, which tells us:
SMI Private Enterprise Codes: Prefix: iso.org.dod.internet.private.enterprise (1.3.6.1.4.1) See http://www.iana.org/assignments/enterprise-numbers
which I do and where I find that enterprise-number 311 was assigned to Microsoft. They have a nice knowledge-base article which lists some Object IDs, but no information on the subtree ’60’.
So dear Redmond, what about an update to that page?