The Austrian ISP Association (ISPA) had asked me to hold a workshop on DNSSEC as part of their “ISPA Academy” series of events. And as they had complaints that all their events are in Vienna, I agreed to hold it in Salzburg, where I had logistical support from the nic.at headquarter.
I thus spent the Wednesday traveling to Salzburg (actually: I’m usually quite productive in trains, and a good part of the presentation was prepared on the way in), then holding the workshop and riding the train back. Six hours of train for 4 hours of workshop isn’t that bad.
If anyone is interested, here are my slides. My aim was to explain the motivation for DNSSEC, the technical implementation and, most importantly, what introducing DNSSEC means for an ISP. I only touched very briefly on the commercial aspect.
In the end, this room full of techies were not exactly cheering for the adoption of dnssec.
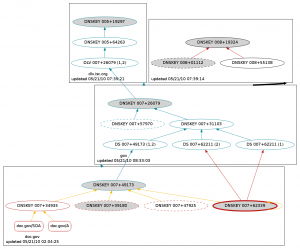
Postscript: Just two days later, we have this: doc.gov, the entity that still has a hand in approving changes to the root zone, messed up their DNSSEC signatures. From http://dnsviz.net/d/doc.gov/dnssec/: